OCI Vault Sync is a paid feature.If you’re using Infisical Cloud, then it is available under the Enterprise Tier. If you’re self-hosting Infisical,
then you should contact team@infisical.com to purchase an enterprise license to use it.
- Create an OCI Connection with the required Secret Sync permissions
- Create or use an existing OCI Compartment (which the OCI Connection is authorized to access)
- Create or use an existing OCI Vault
- Ensure your network security policies allow incoming requests from Infisical to this secret sync provider, if network restrictions apply.
1
Add Sync
Navigate to Project > Integrations and select the Secret Syncs tab. Click on the Add Sync button.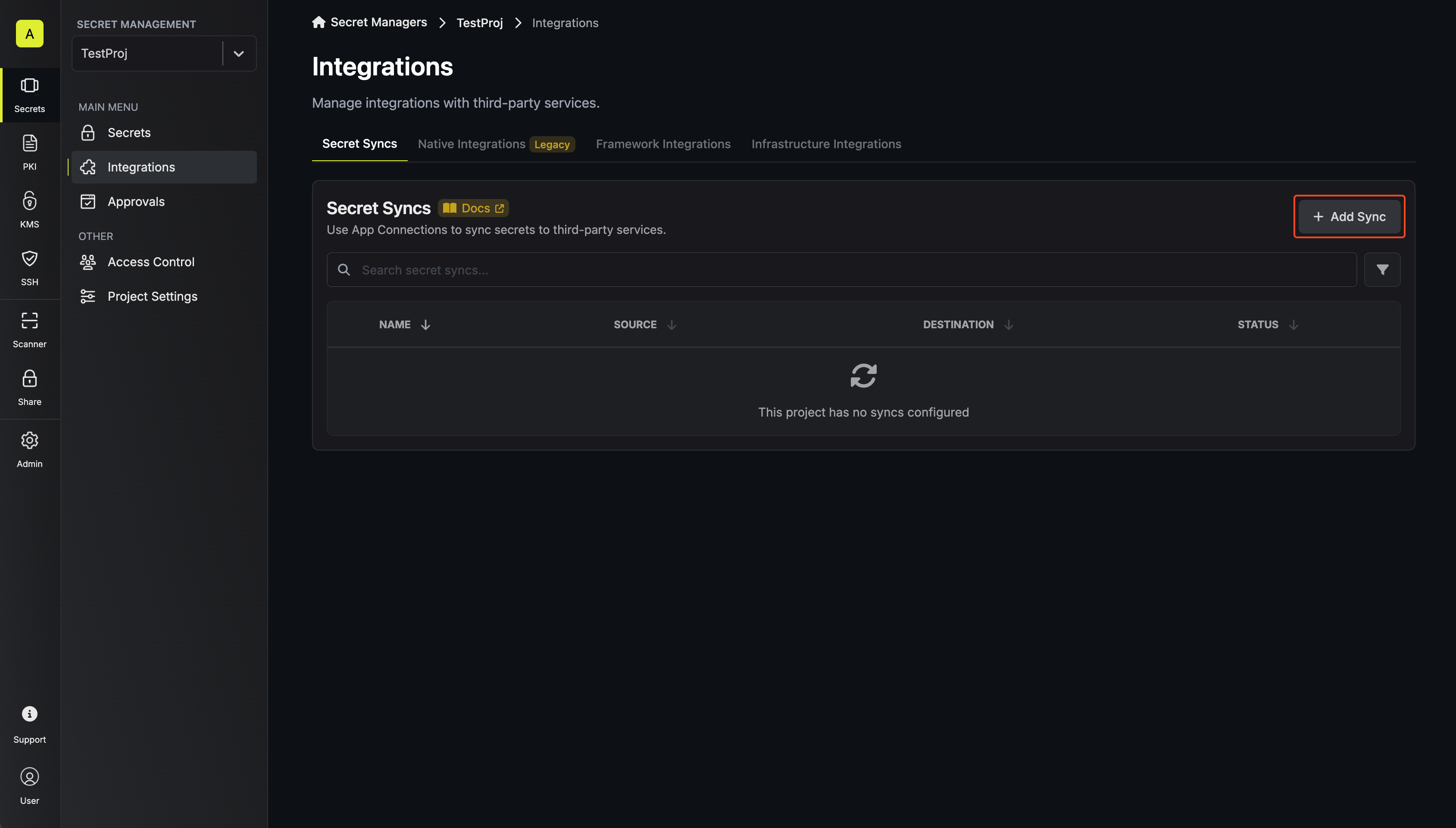

2
Select 'OCI Vault'
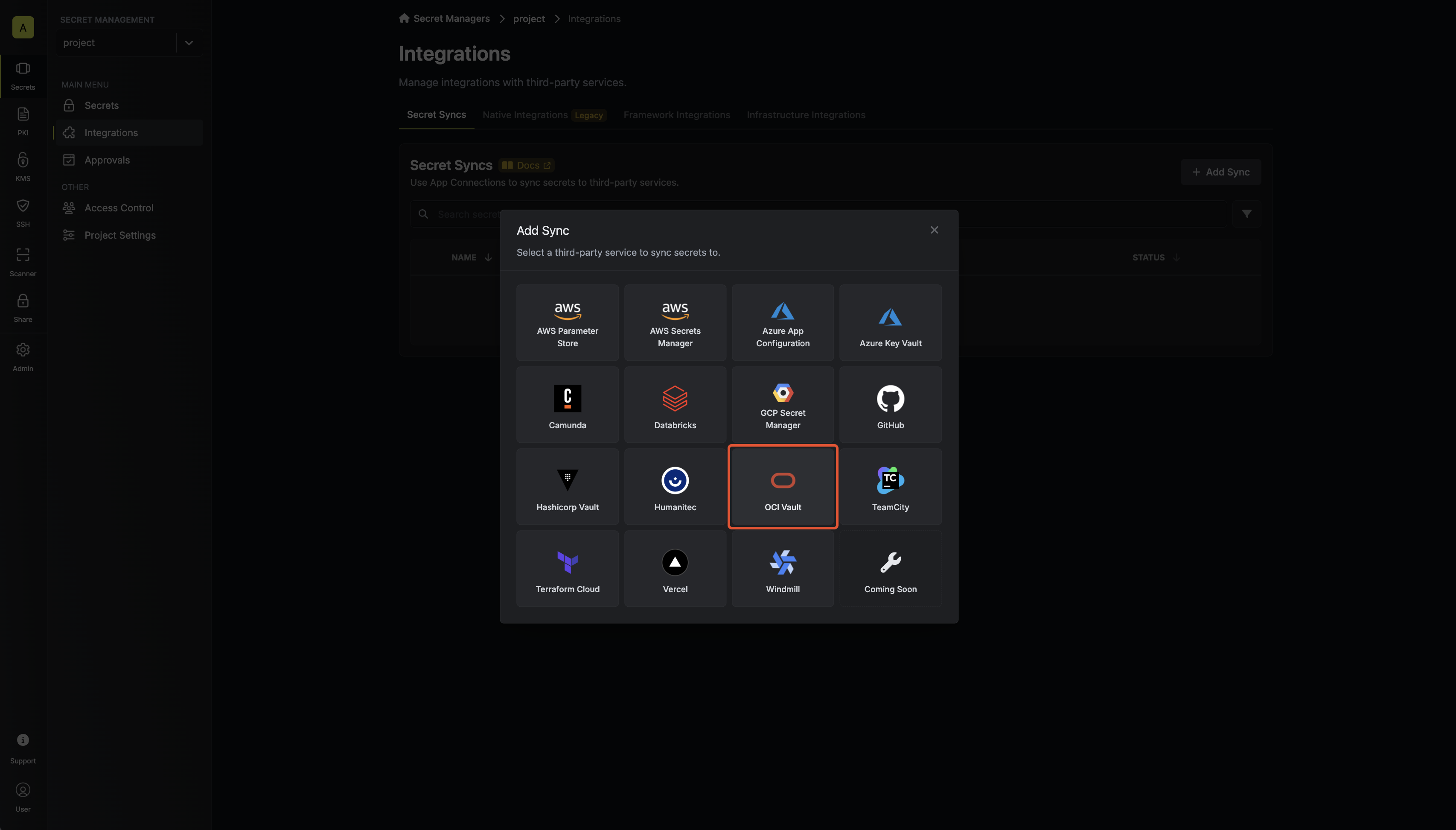
3
Configure source
Configure the Source from where secrets should be retrieved, then click Next.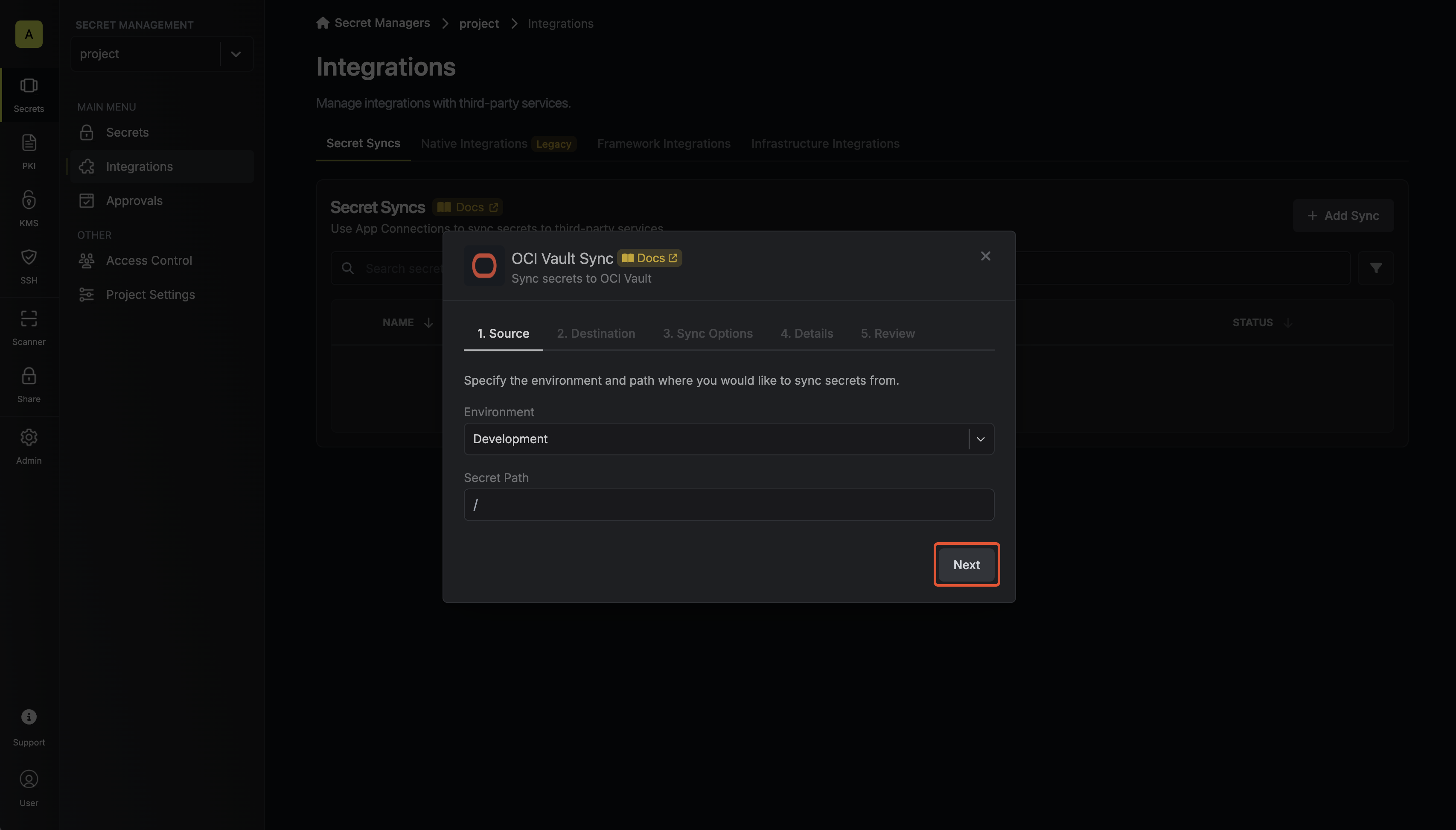

- Environment: The project environment to retrieve secrets from.
- Secret Path: The folder path to retrieve secrets from.
If you need to sync secrets from multiple folder locations, check out secret imports.
4
Configure destination
Configure the Destination to where secrets should be deployed, then click Next.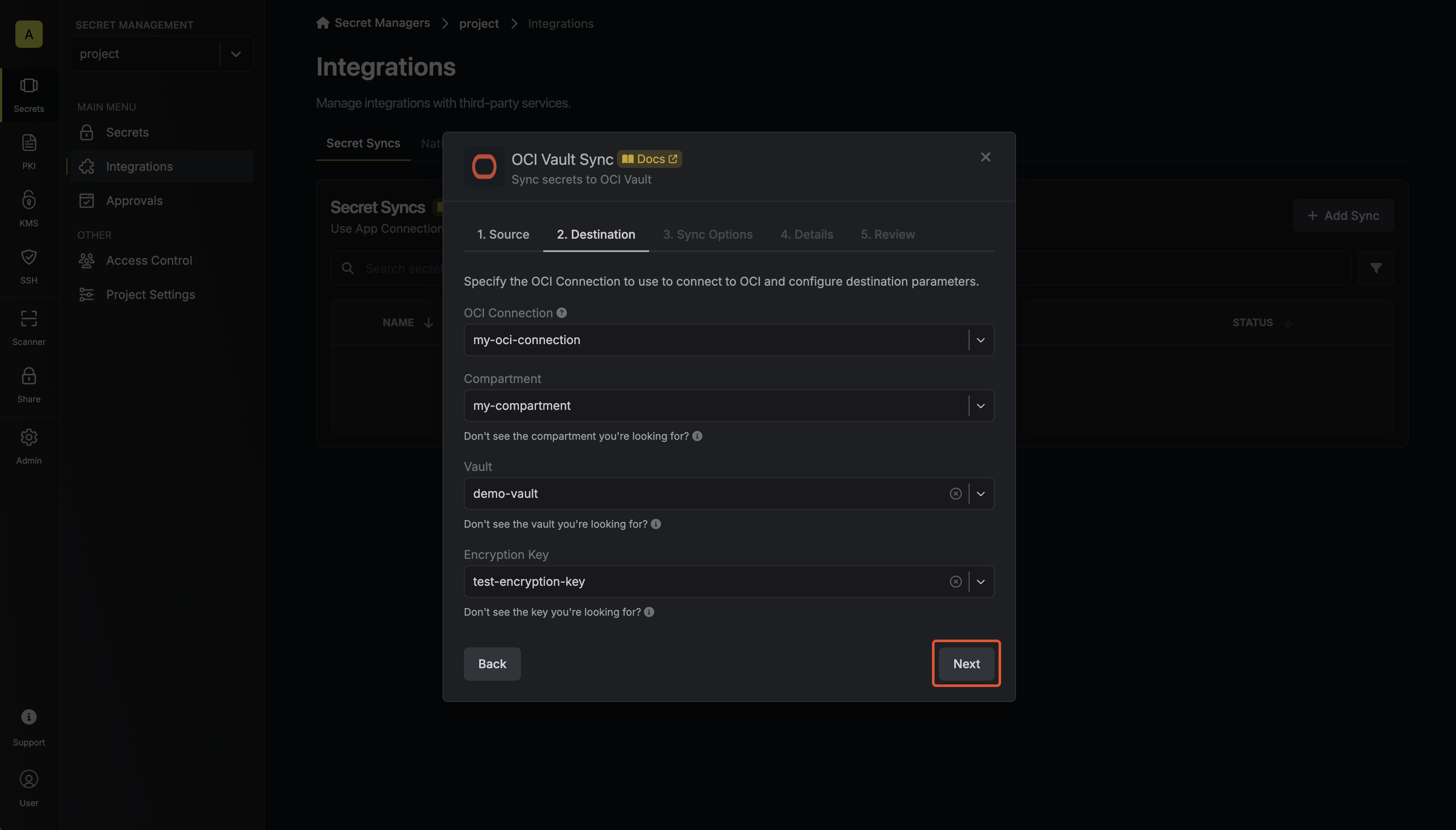

- OCI Connection: The OCI Connection to authenticate with.
- Compartment: The compartment where the vault is located.
- Vault: The vault to sync secrets to.
- Encryption Key: The encryption key to use when creating secrets in the vault.
5
Configure sync options
Configure the Sync Options to specify how secrets should be synced, then click Next.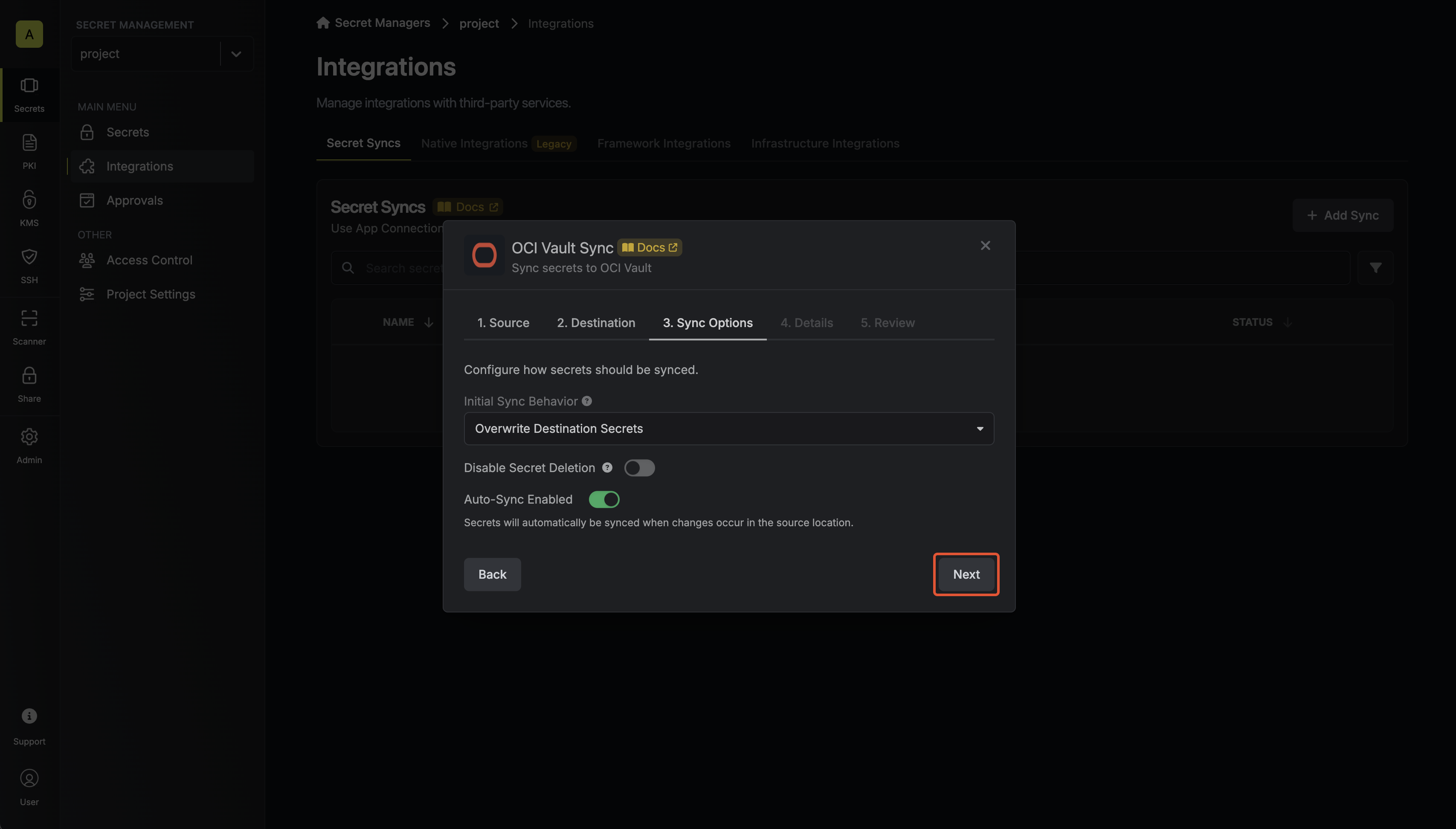

- Initial Sync Behavior: Determines how Infisical should resolve the initial sync.
- Overwrite Destination Secrets: Removes any secrets at the destination endpoint not present in Infisical.
- Import Secrets (Prioritize Infisical): Imports secrets from the destination endpoint before syncing, prioritizing values from Infisical over OCI Vault when keys conflict.
- Import Secrets (Prioritize OCI Vault): Imports secrets from the destination endpoint before syncing, prioritizing values from OCI Vault over Infisical when keys conflict.
- Key Schema: Template that determines how secret names are transformed when syncing, using
{{secretKey}}as a placeholder for the original secret name and{{environment}}for the environment.
We highly recommend using a Key Schema to ensure that Infisical only manages the specific keys you intend, keeping everything else untouched.
- Auto-Sync Enabled: If enabled, secrets will automatically be synced from the source location when changes occur. Disable to enforce manual syncing only.
- Disable Secret Deletion: If enabled, Infisical will not remove secrets from the sync destination. Enable this option if you intend to manage some secrets manually outside of Infisical.
6
Configure details
Configure the Details of your OCI Vault Sync, then click Next.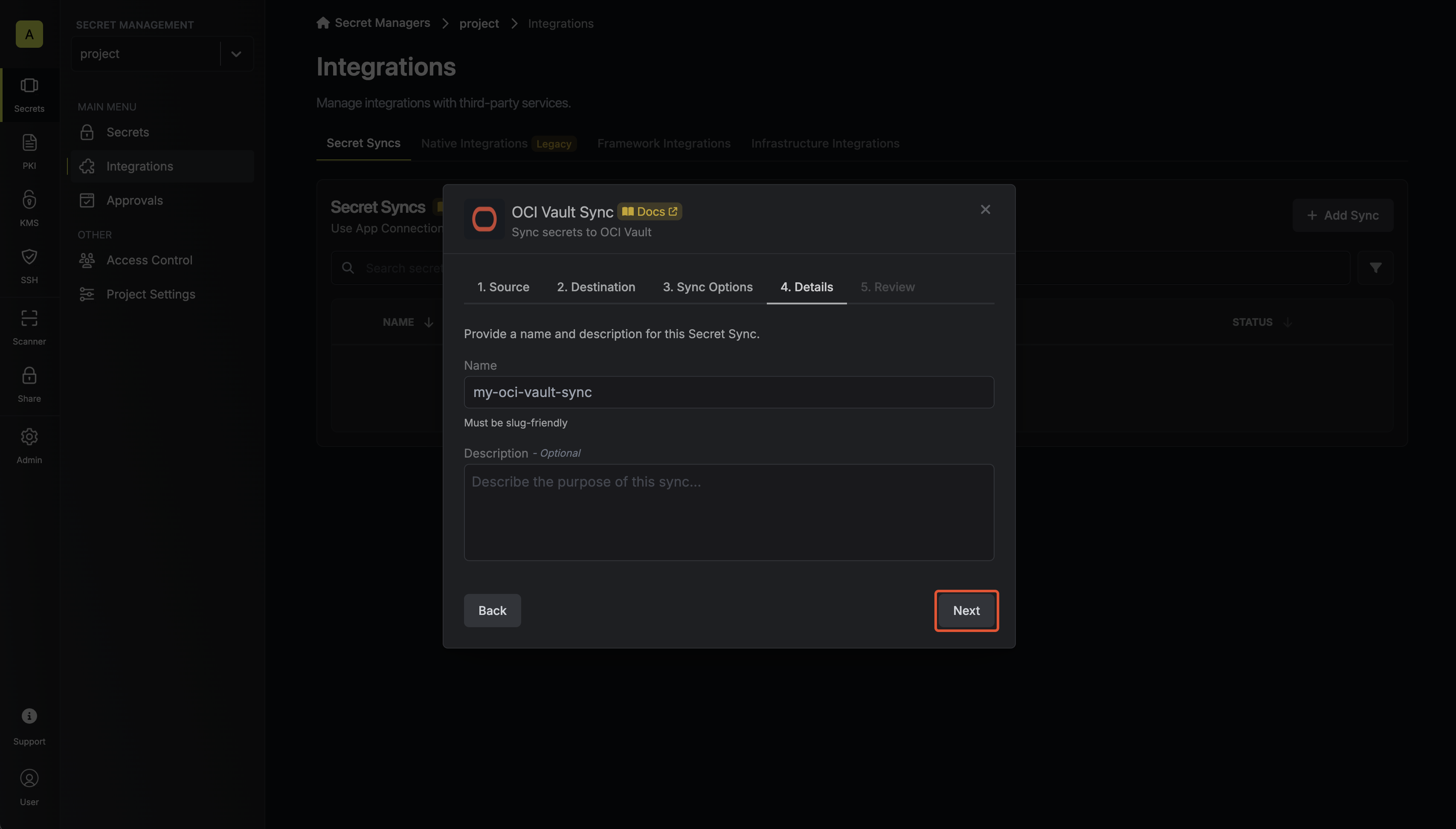

- Name: The name of your sync. Must be slug-friendly.
- Description: An optional description for your sync.
7
Review configuration
Review your OCI Vault Sync configuration, then click Create Sync.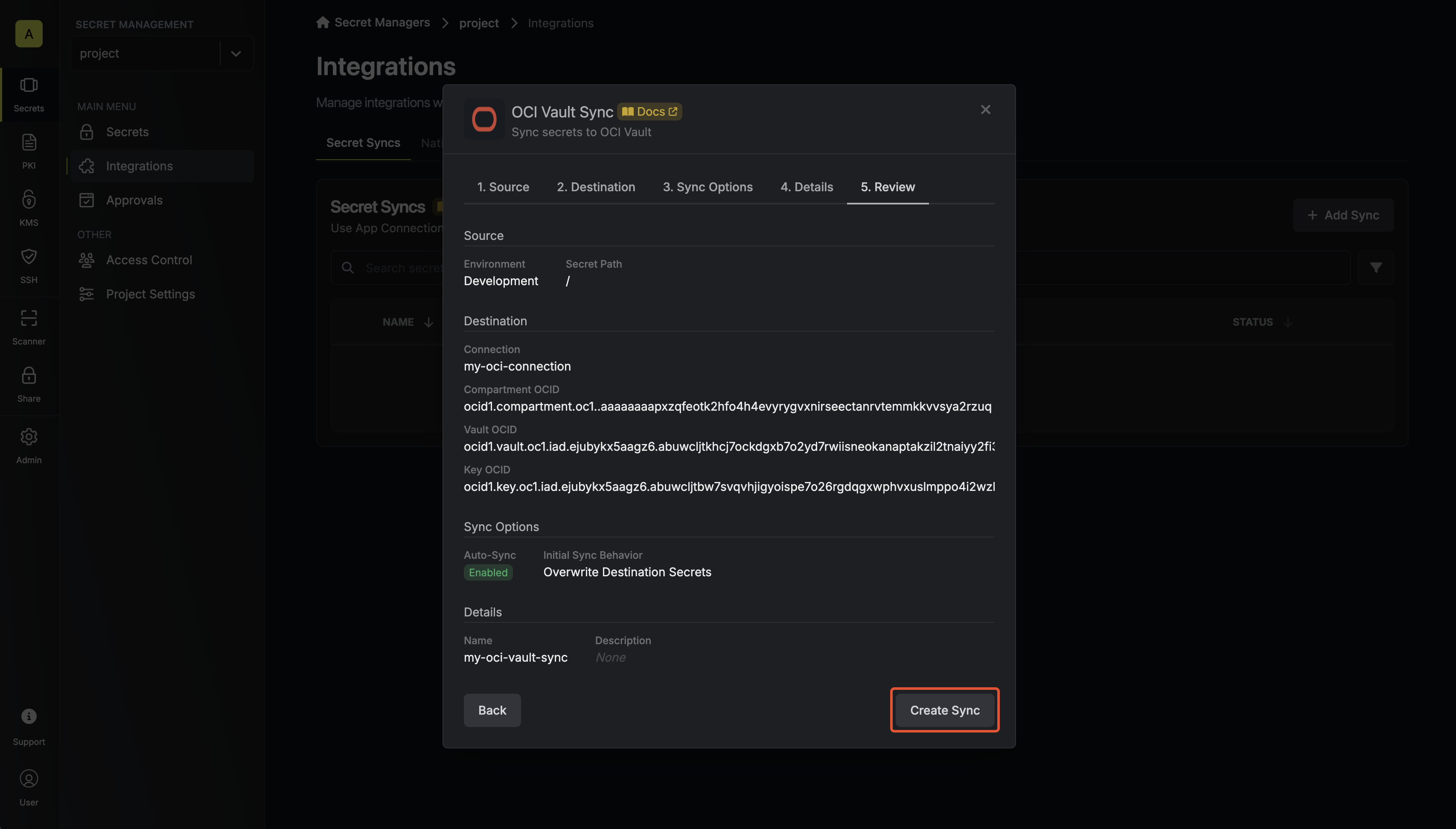

8
Sync created
If enabled, your OCI Vault Sync will begin syncing your secrets to the destination endpoint.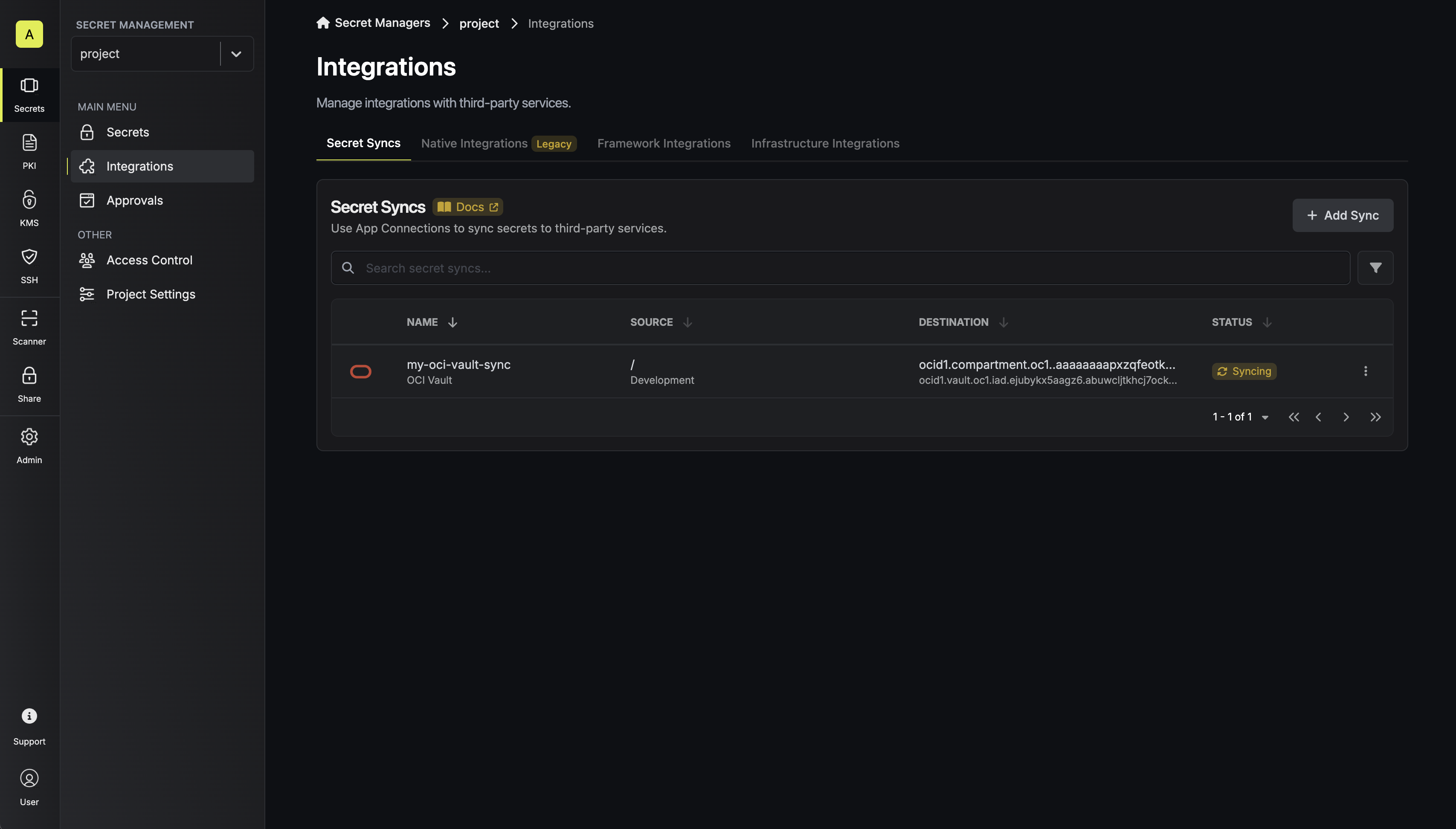

FAQ
How are non-active lifecycle states treated?
How are non-active lifecycle states treated?
When Infisical attempts to sync secrets, the sync will fail and attempt to re-sync if any secret has one of the following lifecycle states:
- SchedulingDeletion
- CancellingDeletion
- Deleting
- Creating
- Updating
What happens if I create / update a variable that's scheduled for deletion in OCI Vault?
What happens if I create / update a variable that's scheduled for deletion in OCI Vault?
In the case that a variable is created or updated while it’s scheduled for deletion in OCI Vault, we cancel the deletion and update the variable. This action may take up to a minute since Infisical must wait for OCI to completely cancel the deletion and then update the variable.

