Introduction
Monitor and detect exposed secrets across your data sources, including code repositories, with Infisical Secret Scanning. For additional security, we recommend using our CLI Secret Scanner to check for exposed secrets before pushing your code changes.Secret Scanning is a paid feature. If you’re using Infisical Cloud, then it is
available under the Enterprise Tier. If you’re self-hosting Infisical,
then you should contact team@infisical.com to purchase an enterprise license
to use it.
How Secret Scanning Works
Secret Scanning consists of several components that enable you to quickly respond to secret leaks:- Scanner Engine: The core component that analyzes your code and detects potential secrets using pattern matching and entropy analysis
- Real-time Monitoring: Provides continuous surveillance of your repositories for immediate detection of exposed secrets
- Alert System: Notifies organization admins via email when secrets are detected
- Risk Management: Allows tracking and managing detected secrets with different status options
- Data Sources: Integrates with various data sources and version control systems
- Customizable Rules: Supports ignore patterns and custom configurations to reduce false positives
Data Sources
Data sources are configured integrations with external platforms, such as a GitHub organization or a GitLab group, that establish secure connections for scanning purposes using App Connections. A data source acts as a secure intermediary between the external system and the scanner engine. It manages a collection of scannable resources (such as repositories) and handles the authentication and communication required for scanning operations.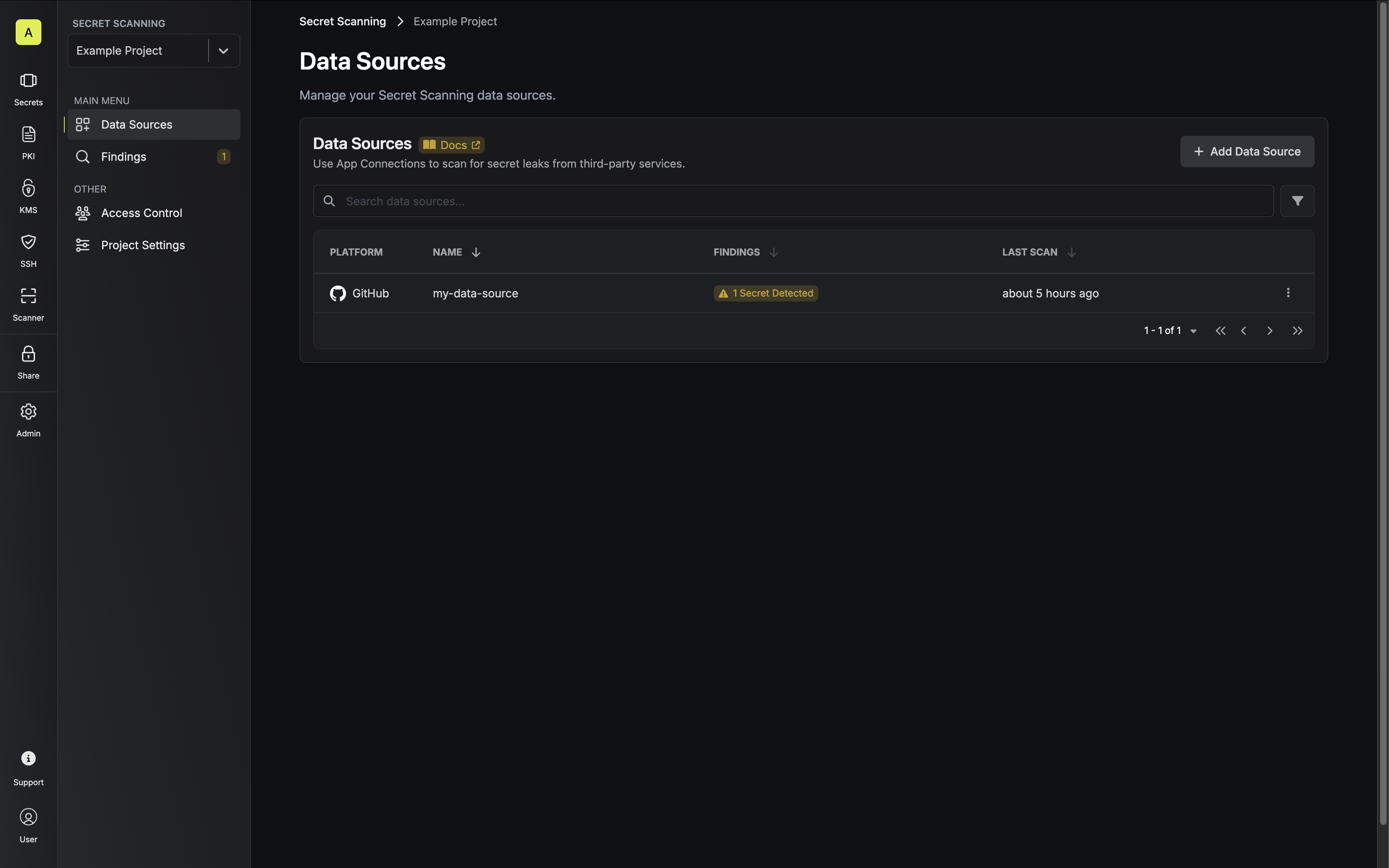
Resources
Resources are the atomic, scannable units, such as a repository, that can be monitored for secret exposure. Resources are added automatically when a data source is scanned and updated when scanning events are triggered, such as when a user pushes changes to GitHub. Each resource maintains its own scanning history and status, allowing for granular monitoring and management of secret scanning across your organization.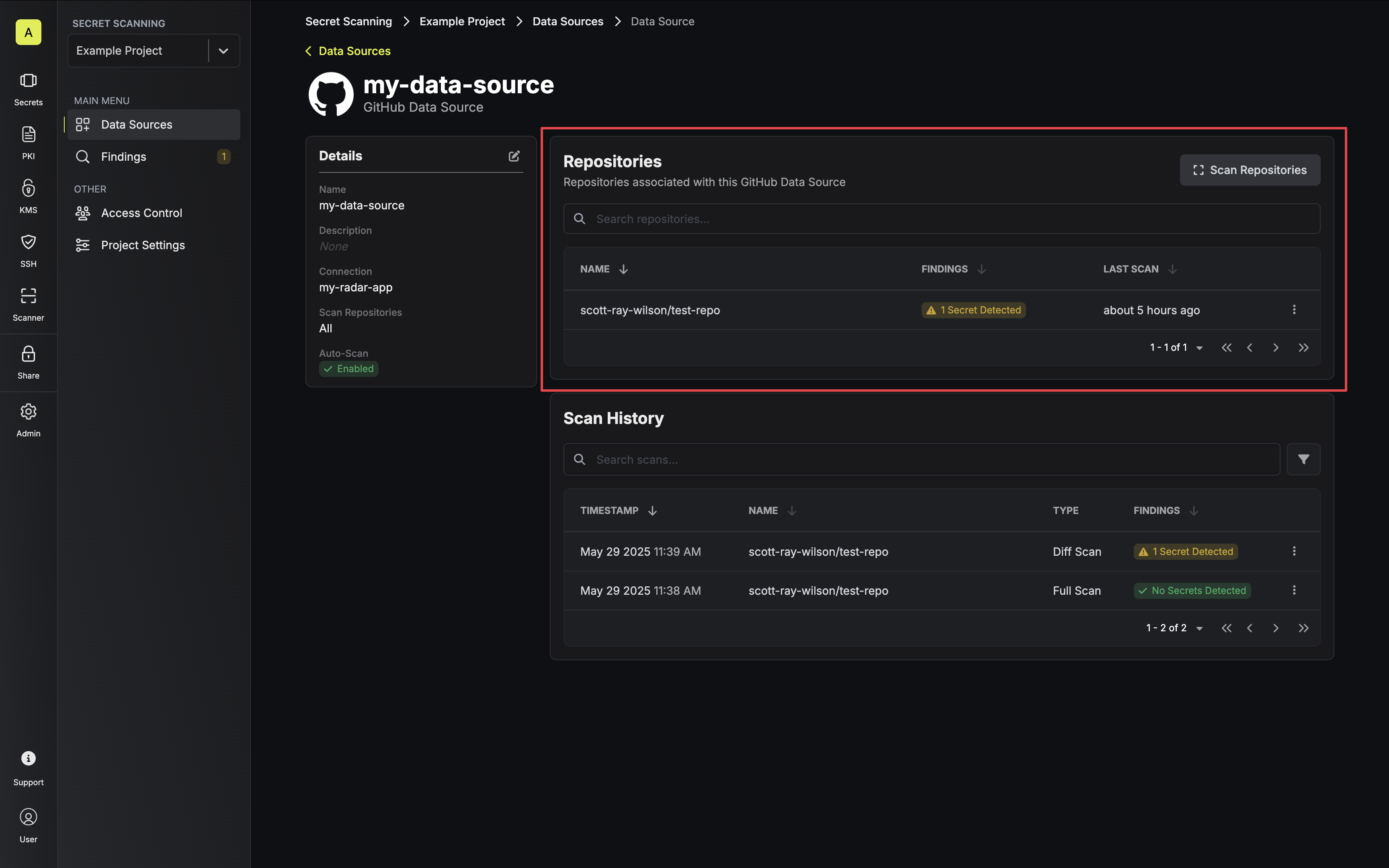
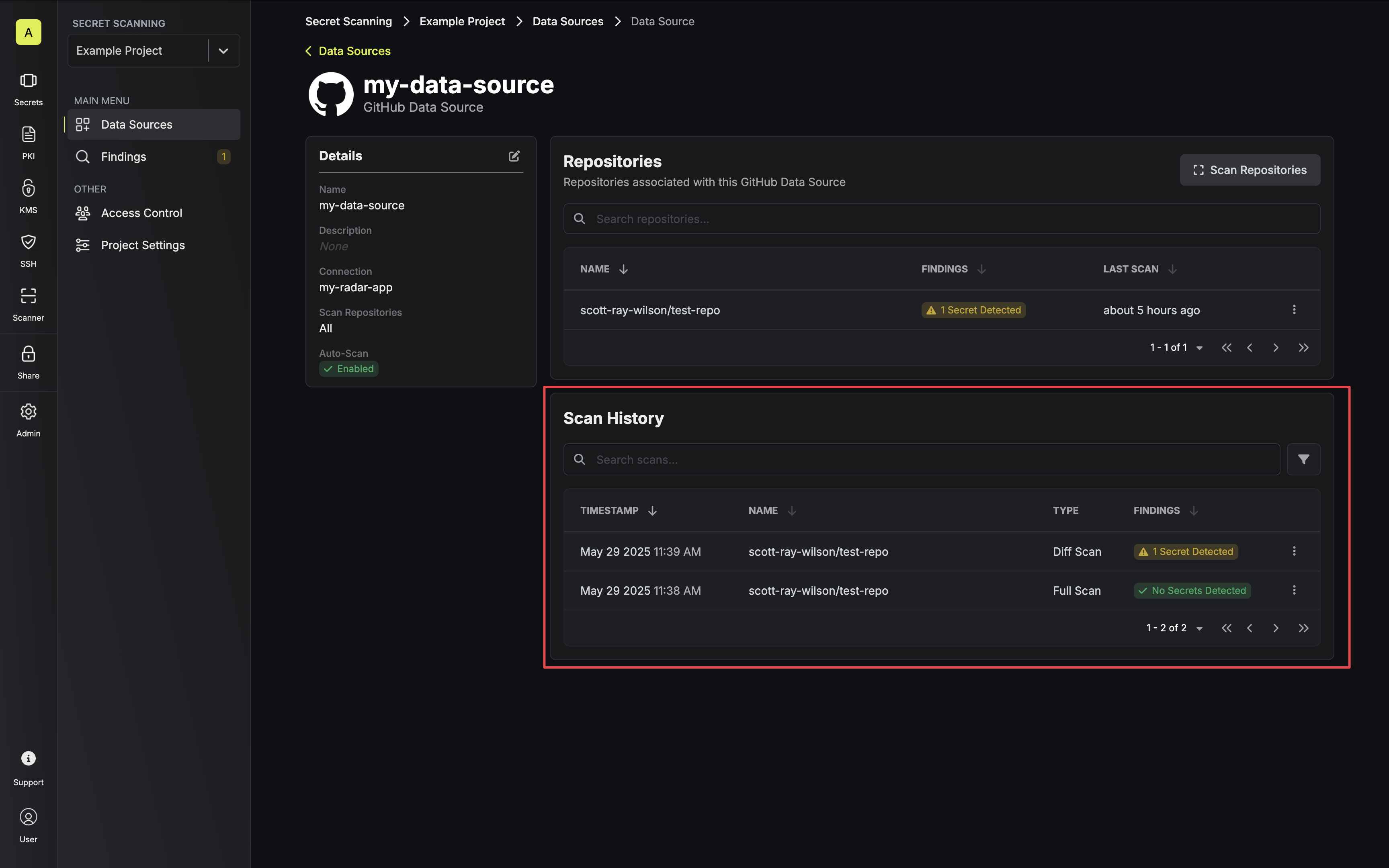
Scans
Scans can be initiated in two ways:- Full Scan - Manually triggered scan that comprehensively checks either all resources associated with a data source or a single selected resource.
- Diff Scan - Automatically executed when Auto-Scan is enabled on a data source. This scan type specifically focuses on updates to existing resources.
- Current scan status
- Timestamp of the scan
- Resource(s) being scanned
- Detection results (whether any secrets were found)
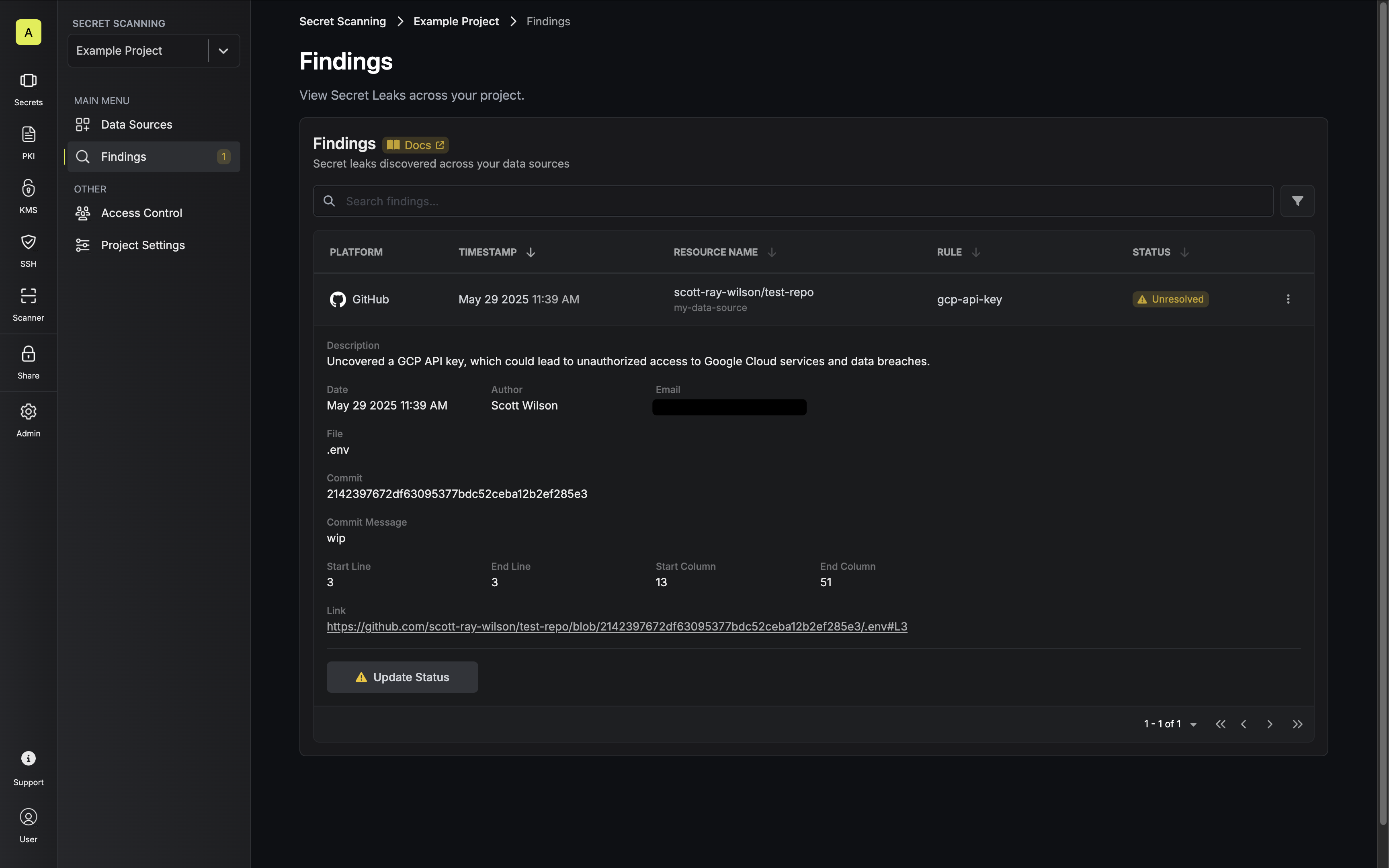
Findings
Findings are automatically generated when secret leaks are detected during scanning operations. Each finding contains comprehensive information including:- The specific scanning rule that identified the leak
- File location and line number where the secret was found
- Resource-specific details (e.g., commit hash and author for Git repositories)
- Resolved - The issue has been addressed
- False Positive - The detection was incorrect
- Ignore - The finding can be safely disregarded
Configuration
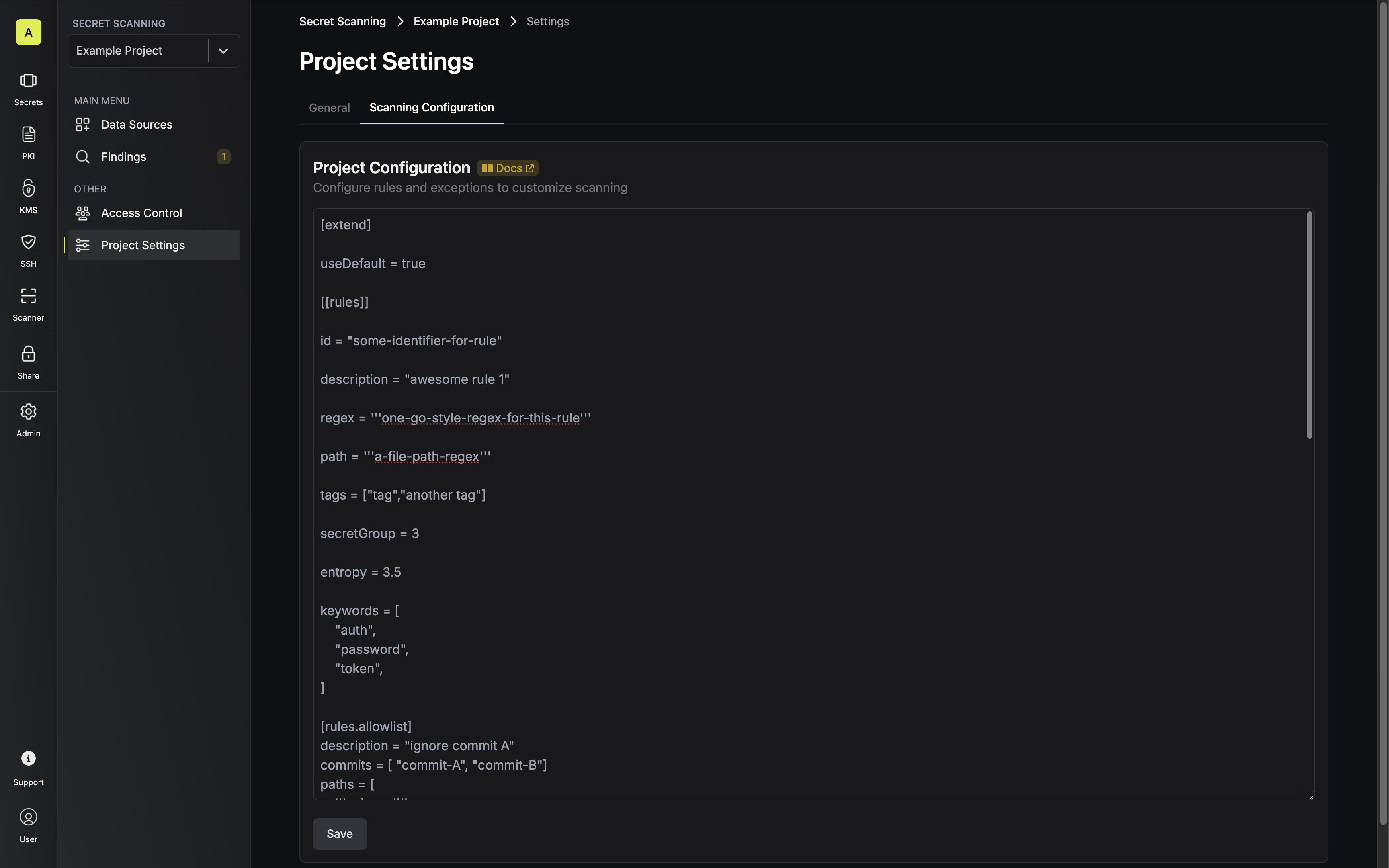
You can configure custom scanning rules and exceptions by updating your project’s scanning configuration via the UI or API. The configuration options allow you to:- Define custom scanning patterns and rules
- Set up ignore patterns to reduce false positives
- Specify file path exclusions
- Configure entropy thresholds for secret detection
- Add allowlists for known safe patterns
Example Configuration
Example Configuration
Ignoring Known Secrets
If you’re intentionally committing a test secret that the secret scanner might flag, you can instruct Infisical to overlook that secret with the methods listed below.infisical-scan:ignore
To ignore a secret contained in line of code, simply addinfisical-scan:ignore at the end of the line as comment in the given programming.
example.js
.infisicalignore
An alternative method to exclude specific findings involves creating a .infisicalignore file at your repository’s root. You can then add the fingerprints of the findings you wish to exclude. The Infisical scan report provides a unique Fingerprint for each secret found. By incorporating these Fingerprints into the .infisicalignore file, Infisical will skip the corresponding secret findings in subsequent scans..infisicalignore

