-
A project administrator sets up an access policy that assigns access managers (also known as eligible approvers) to a certain sensitive folder or environment.
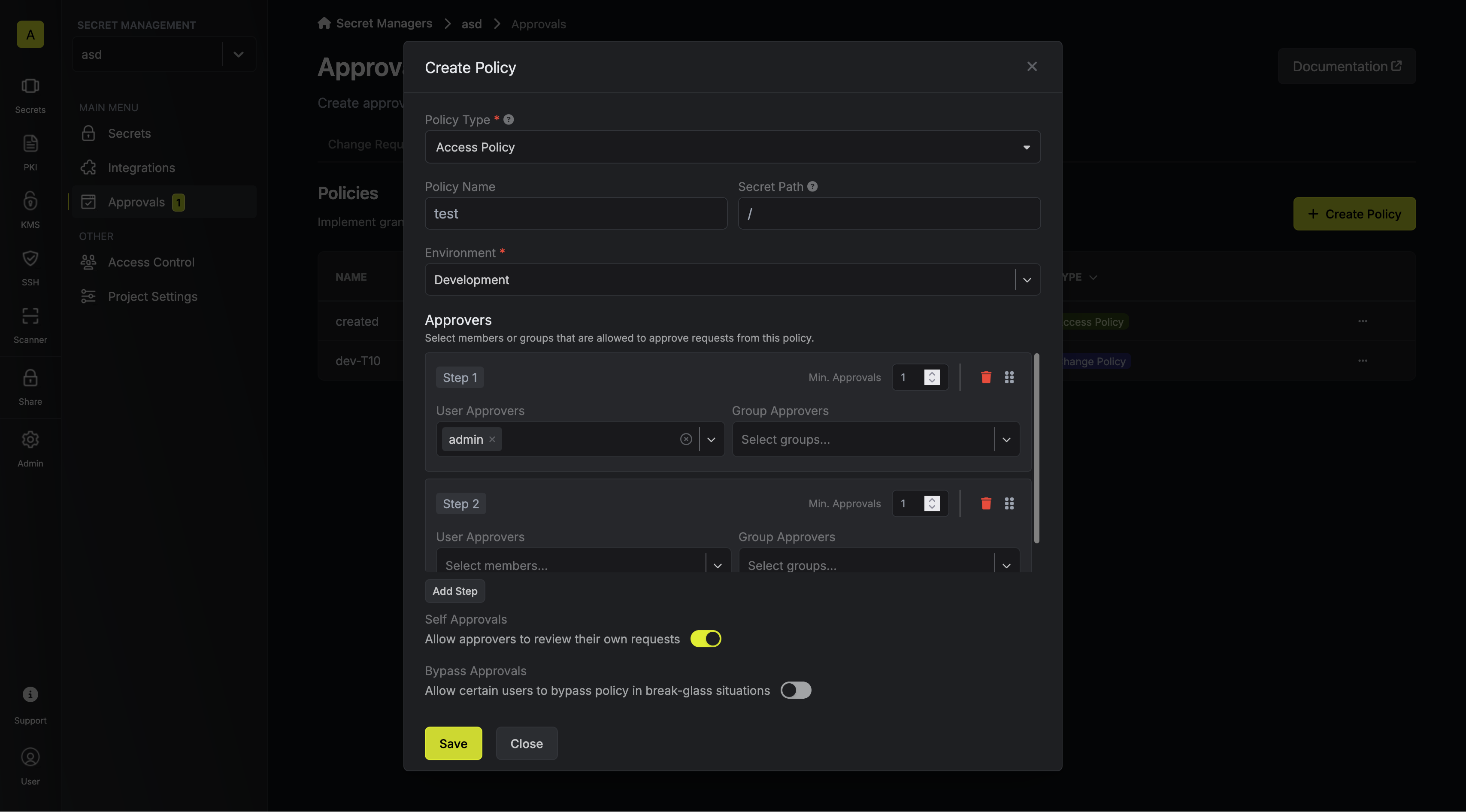 A step policy enables a sequential approval workflow in which approvals must follow the designated chain.
A step policy enables a sequential approval workflow in which approvals must follow the designated chain.
-
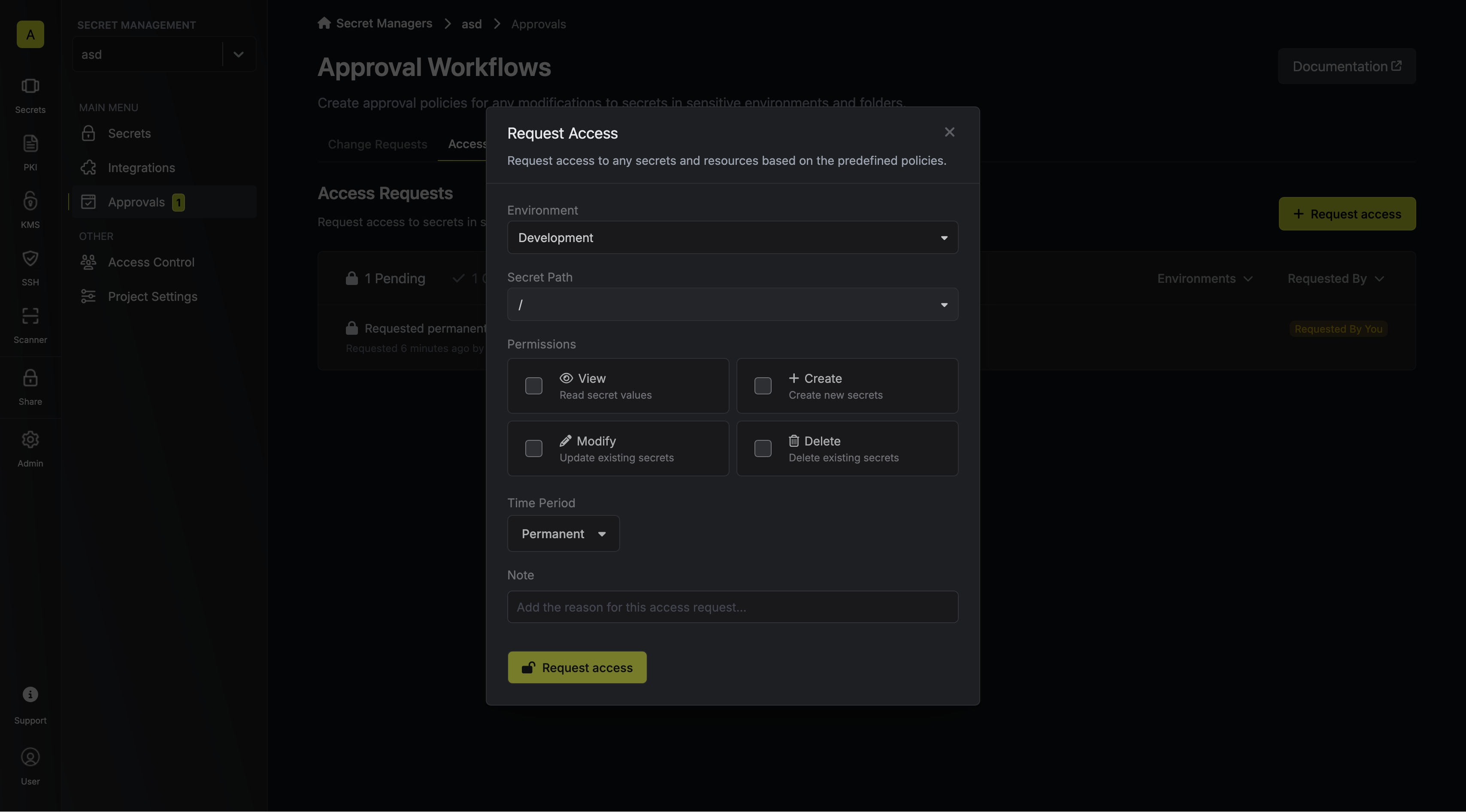
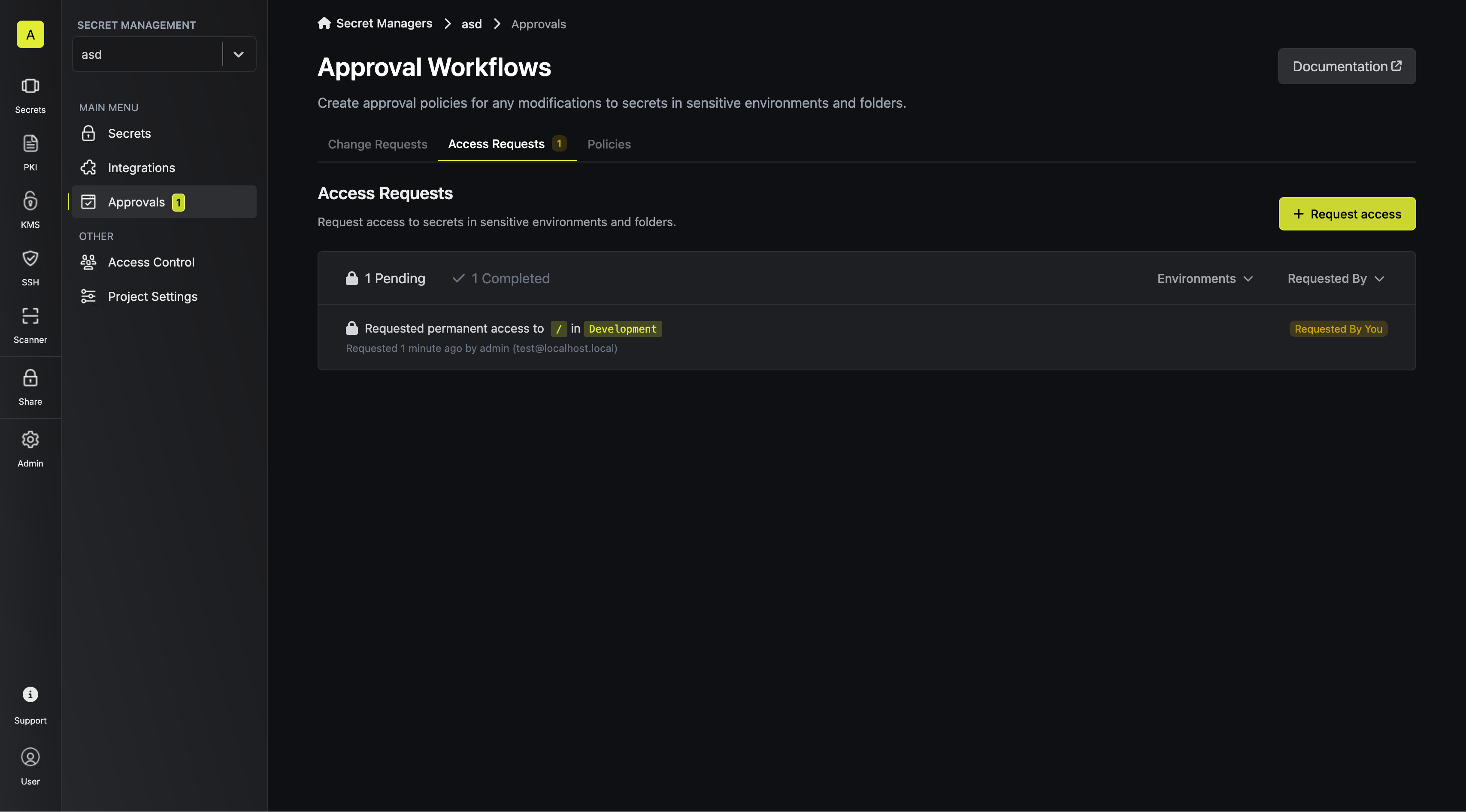
When a developer requests access to one of such sensitive resources, the request is visible in the dashboard, and the corresponding eligible approvers get an email notification about it.
-
An eligible approver can approve or reject the access request.
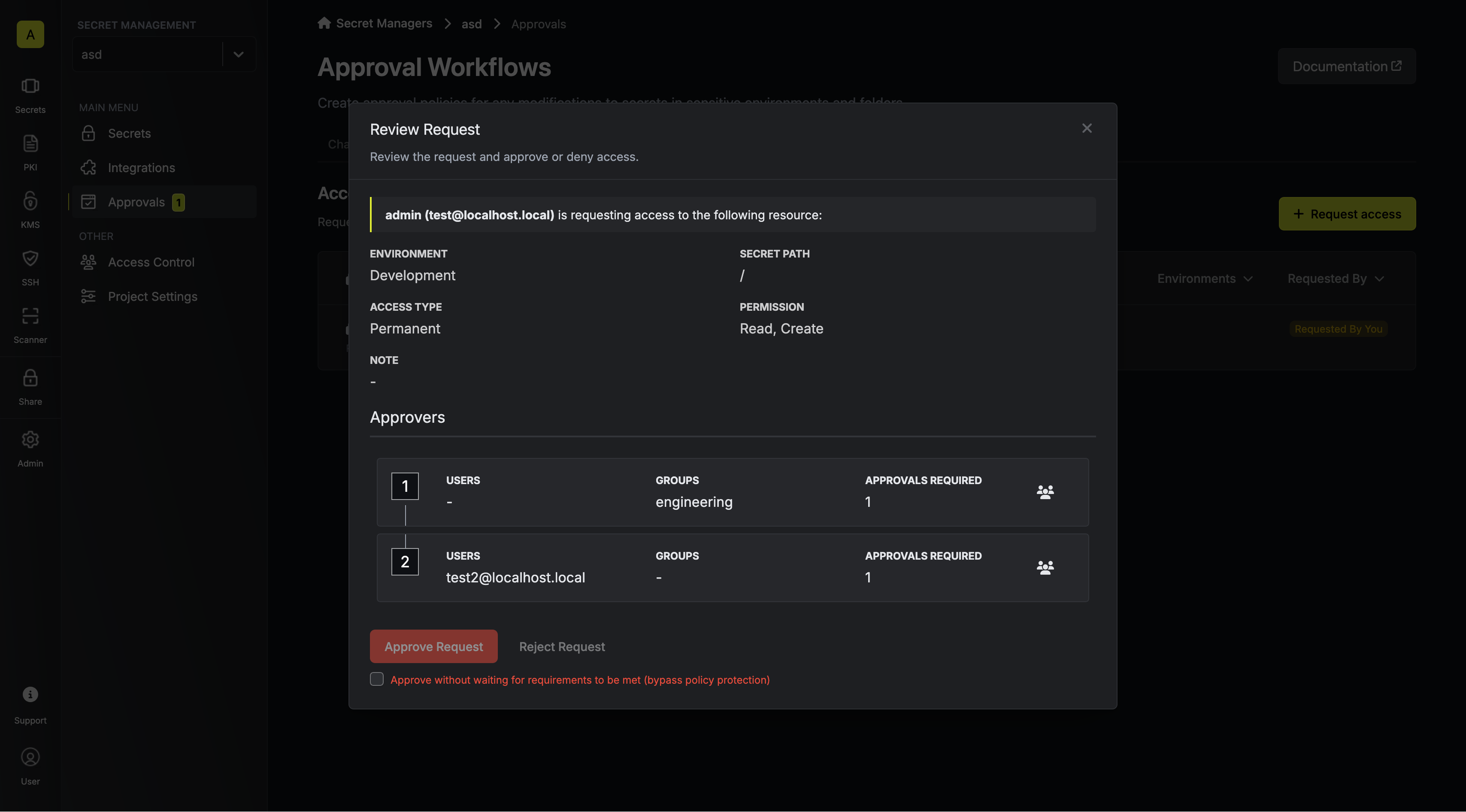
If the access request matches with a policy that allows break-glass approval
bypasses, the requester may bypass the policy and get access to the resource
without full approval.
- As soon as the request is approved, developer is able to access the sought resources.

